UCL Research Data Information Security Management System Roles and Responsibilities #
Document Name: RISM02-Roles_and_Responsibilities
Classification: Public
Author: Tim Machin
version: 5.2
Last Review: 04/04/2025
Last Reviewed by: Sulyman Abdulkareem
Approved by: OMG
Approved date: 12/03/2025
Review Period: 3 years
Sources: SLMS-IG05, SLMS-IG07, SLMS-IG16, SLMS-IG32
1. Document Overview #
This document establishes the framework for defining roles, responsibilities, and authorities within the UCL Research Data Information Security Management System (’the ISMS’). It also outlines our approach to providing those roles with appropriate resources, ensuring the competence of the persons assigned to those roles, and promoting awareness of information security throughout the organisation.
This document also outlines the framework for identifying the necessary resources and competencies required for each of the above groups, ensuring they can establish, implement, maintain and continuously improve the ISMS.
This document covers:
- Scope of the roles and responsibility
- The information governance framework
- How resources are allocated
- Competencies expected
- The Shared responsibility Model
- Approved researcher, study and project roles
- Complete roles catalogue
This document addresses the following requirements in the ISO 27001:2022 standard:
- Clause 5.3
- Clause 7.1
- Clause 7.2
2. Scope of the roles and responsibilities #
This document applies to all groups and group members within the scope detailed in the Research Data ISMS Scope, including researchers, governance groups, IT service delivery teams and UCL-wide functions.
This document also outlines the framework for determining the appropriate resources and competencies that are to be available to, or possessed by, the members of each of the above groups, enabling them to establish, implement, maintain, and continually improve the ISMS.
3. The Information Governance Framework #
The high-level structure of the ISMS’s Information Governance Framework is represented in the diagram below.
3.1 Top Management #
The ISMS Top Management consists of UCL’s Senior Information Risk Owner (SIRO) and the Information Risk Governance Committee (IRGC), chaired by the SIRO. The SIRO is a UCL executive and reports to the University Management Committee (UMC), providing a direct reporting line from the ISMS to UCL’s primary body responsible for operational management, which oversees institute strategy, risk management, and key policies. The SIRO receives assurance that relevant processes, procedures and policies are in place to protect UCL’s information assets. The IRGC receives reports from the Operational Management Group (OMG), holds them to account, and in turn provides advice and assurances to the SIRO.
3.2 Operational Management Group (OMG) #
The OMG reports to the IRGC to assure that the ISMS is operating effectively, delivering information security objectives and managing information risks within tolerance. While the OMG is responsible for ISMS policies, it may escalate risks to IRGC that cannot be resolved directly by the OMG. Risk decisions are therefore ultimately owned by the IRGC.
The OMG is composed of members of the ISMS’s governance, technical, and service teams. Full details of membership and responsibilities of individual roles can be found in the OMG Terms of Reference.
The Trusted Research Environments (TREs) (as defined in the classification and tiering policy) that form part of the scope and are managed by the UCL Information Services Division (ISD) and the Centre for Advanced Research Computing (ARC). They are represented at the OMG to ensure these Environments are operating safely.
4. Resources #
Funding for ISMS and all technical environments (TREs) is provided by the UCL Change and Digital Committee structure. Top management requests funding from the Change and Digital Committee in the form of business cases. Top Management ensures sufficient resources are available. Where resource constraints pose risks to the organisation, top management escalates to UMC.
5. Competence #
UCL determines the necessary competence of persons doing work under its control that affects its information security performance, including staff, suppliers, and researchers, and ensures they are competent to perform this work.
Staff competence and suitability are determined as part of the recruitment and selection procedure.
All users must complete suitable information governance training. This training must be kept up to date; failure to do so may result in losing access to the Trusted Research Environments. A list of acceptable training courses can be found in Annex A, and the required competence for each role is detailed in the roles catalogue.
The training listed in the roles catalogue below is determined through a training needs analysis. Approved researcher training ensures it meets the requirements of our key data providers, such as the NHS. UCL-wide training is mandatory and designed by the UCL Information Security Group to meet the requirements of UCL’s obligations to data subjects.
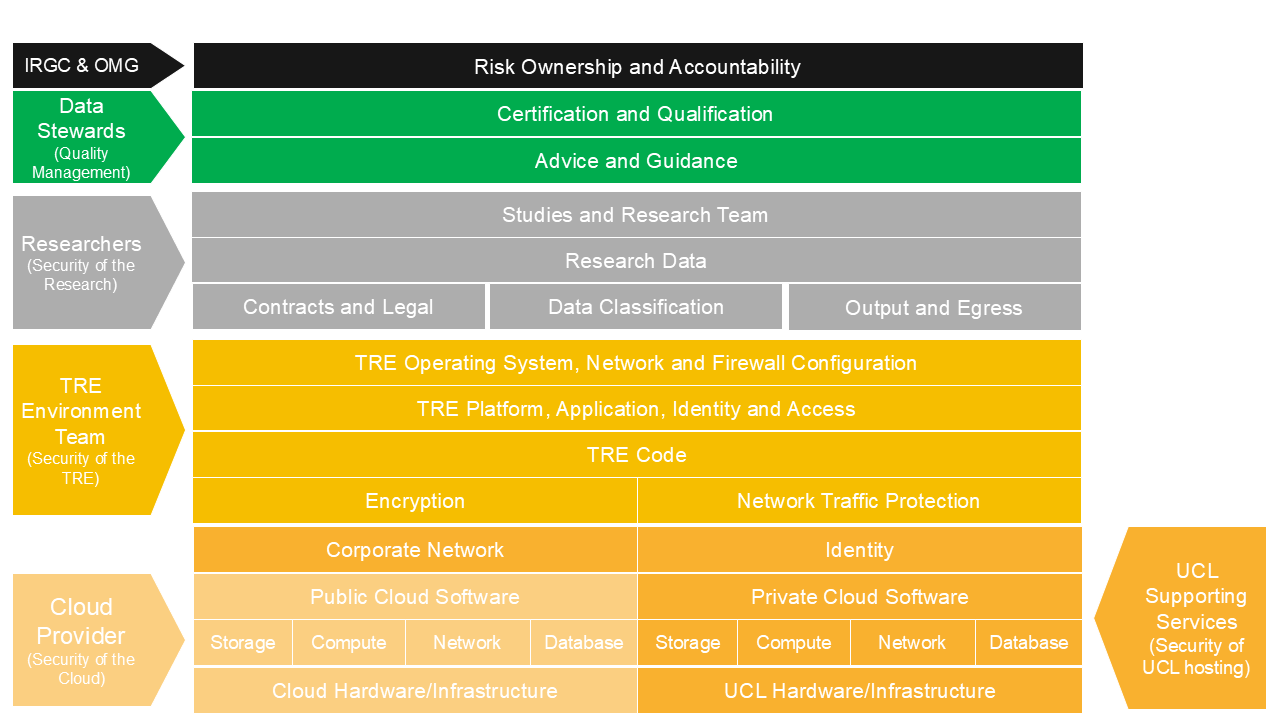
6. Shared Responsibility Model #
Security and compliance are shared responsibilities among infrastructure providers, environment providers, research teams, and data stewards. The model below provides an overview of how these responsibilities are allocated.
7. Approved Researcher, Study and Project Roles #
Users of the TREs are authorised through the following structure and per the Access Control Policy
| Term | Definition |
|---|---|
| Study | A study is an Information Governance construct and exists to manage the risk and ownership of specific data.Each study has an Information Asset Owner that owns that study. The Information Asset Owner can create one or more project spaces attached to that study. |
| Project | A Project is a permissions boundary within a technical environment. This is where the whole or a subset of the parent study’s data is stored and processed by members of the research team.Access to data within a project is managed through permissions determined by the Information Asset Owner or the Information Asset Administrator. |
7.1. Approved Researcher Role #
Approved researcher roles have no access to data by default within any project, Approved researchers can apply to create Studies (see below) or access projects. An approved researcher must provide evidence that they have up-to-date approved information governance training and sign an approved researcher agreement.
An approved researcher must be covered by a legal agreement, for example, a staff contract (for UCL staff) or a research contract (for external collaborators).
7.2. Study Roles #
Study roles have no access to data within projects by default.
At the study level, users can be assigned the role of an Information Asset Owner, who is responsible for owning a ‘study’.
The Information Asset Owner is accountable for any confidential information processed by project users and is accountable for the safe use of that information. An Information Asset Owner must sign and comply with the responsibilities detailed in the Study Agreement.
An Information Asset Owner may delegate responsibility (while retaining overall accountability) for the day-to-day management of users and projects to an Information Asset Administrator. Information Asset Administrator responsibilities as detailed in the roles catalogue.
Information Asset Owners and Information Asset Administrators must be both substantive (full) members of UCL staff and approved researchers.
7.3. Project Roles #
Project roles have access to data within projects as approved by the Information Asset Owner or Information Asset Administrator.
A project is a permissions boundary inside which data is stored and processed. All project users must be provided access to that specific project by the Information Asset Owner or Information Asset Administrator.
Users of a TRE will only be granted access once they have been designated an “Approved Researcher” and can be members of UCL staff, students, visitors or external collaborators.
Users may have different permissions within a project assigned by the Information Asset Owner or the Information Asset Administrator. For example, some users will have write access to data, while others may be limited to read-only access.
All study and project users are encouraged to participate as members of the research community, raising issues and requesting improvements to the environment.
8. Roles Catalogue #
| User Roles | ||
|---|---|---|
| Role | Responsibilities | Competency and Awareness Requirement |
| Approved Researcher | A “safe” person. Defined by contracts, attestations and competency (training).Must complete training and sign an approved researcher agreement which sets out responsibilities | Approved researcher trainingComplete approved researcher agreementRead and understand relevant policies and procedures. |
| Information Asset Owner | The Information Asset Owner is accountable for any confidential information processed by project users (see below) and for ensuring the safe use of that information. An Information Asset Owner must sign a study agreement. | Be an approved researcherComplete study agreement. |
| Information Asset Administrator | Be responsible for the day-to-day management of users and act with delegated authority from an Information Asset Owner.Information Asset Administrator responsibilities can be found here. | Be an approved researcher. Read and understand Information Asset Administrator responsibilities |
| Project User | Project users have access to some or all data within the boundaries of a project within an environment. Responsibilities for all project users are set out in the approved researcher agreement and any specific requirements of that project related to handling of the data within that project as set out by the Information Asset Owner. Project users can be further subdivided to provide different access within a project. Some examples below:+ Project writer - Can read and write data to shared resources within a specific project+ Project read only - Can read data from shared resources within a specific project+ Project egresser - Can egress “safe” outputs data from a specific TRE project | Be an approved researcher |
| Project Ingress User | A person approved to ingress data to a specific TRE project. This role does not require the approved researcher role and does not have access to any data within the environment, and ingress access can be approved by any project user (via Invite). | None |
| Management | ||
|---|---|---|
| Role | Responsibilities | Competency and Awareness Requirement |
| University Management Committee (UMC) | Oversight of UCL and responsible for setting risk appetite/tolerance. Terms of Reference:Terms of Reference | NA |
| UCL Senior Information Risk Owner (SIRO) | As part of the Information Risk and Governance Committee, the SIRO understands how information risks may impact the strategic academic goals of the organisation and takes ownership of the Research Information Governance Policy. The responsibilities of the SIRO are detailed here | SIRO Training |
| Information Risk Governance Committee (IRGC) | Receives reports from the Operational Management Group, provides advice and assurances to the SIRO and serves as “Top Management” for the Research Data ISMS.Terms of Reference | Members must read and understand ToR |
| Operational Management Group (OMG) | Ensures that effective and informed decisions are made about the operation of the UCL’s Research Data ISMS and that evidence of this is reported to the IRGC. OMG may also escalate risks to IRGC that cannot be resolved by the Group.Terms of Reference | Members must read and understand ToR |
| Governance | ||
|---|---|---|
| Role | Responsibilities | Competency and Awareness Requirement |
| Research Information Governance (IG) Lead | Responsibility for the managerial operation of the UCL Research Data ISMS, Information Governance (IG) Framework, and compliance with the NHS Data Security & Protection (DSP) Toolkit. Provides expertise to and liaises between the SIRO and research teams. Acts as the primary IG contact for all external parties and as a point of escalation for IG matters within UCL.IG Lead Role Description | As detailed as part of recruitment in Job Description, Advert and Interview |
| Information Governance Officer (IG Service Operations Manager) | Operational responsibility for the Research Data ISMS, including but not limited to the maintenance of associated records and the provision of IG training.IG Officer role Description | As detailed as part of recruitment in Job Description, Advert and Interview |
| Internal Auditor | The UCL’s ISMS internal auditor is independent of the ISMS team and is responsible for assessing and reporting on all controls and parts of the standard within the 3-year certification cycle. Internal audits also extend to research teams’ compliance with the standard. | Suitable ISO27001 auditor training |
| Technical and Service | ||
|---|---|---|
| Role | Responsibilities | Competency and Awareness Requirement |
| Environment Owner | Environment owner must:+ Be accountable for the safe development and operation of the trusted research environment they own.+ Describe and maintain the definition of the trusted research environment they own + Be accountable for maintaining the technical controls of the environment + Ensure changes to the technical environment are made safely + Lead on root cause analysis and incident response + Represent the environment during audit + Act in accordance with the responsibilities of a standard product/platform/service owner in ISD/ARC + Approve access to infrastructure management for all environment IT Administrators | Approved Researcher Training |
| Environment Administrator | An environment administrator must: + Be responsible for the safe development and operation of the trusted research environment they administer. + Maintain design and operational documentation around the environment + Be responsible for maintaining the technical controls of the environment + Participate in root cause analysis and incident response + Review and approve contributions from developers | Approved Researcher Training |
| Environment Developer | An environment developer must: + Contribute to the safe development and operation of the trusted research environment they develop. + Implement safe coding practices | None |
| Supporting Service Owner | Where the environment relies on supporting services. The supporting service owner is accountable for the safe running of any supporting component service, such as physical hosting. These will be detailed within the Environment Definition Document. | None |
| UCL Wide Roles | ||
|---|---|---|
| Role | Responsibilities | |
| Chief Information Security Officer (CISO) | Responsible for UCL’s corporate information security agenda. Advises and guides the SIRO on information security matters. Head of the Information Security Group | |
| Information Security Group | Responsible for UCL’s overall stance on information security, including the information security policies, security incident management, and liaison with the police via Estates. | |
| Human Resources (HR) | HR is responsible for UCL’s policies and processes covering recruitment, screening, disciplinary action, and termination of employment. | |
| Change and Digital Committee | Provides resources to maintain and develop the UCL Research Data ISMS and the trusted research environments and information systems. | |
| Data Protection Office | Responsible for providing key information for all staff, students and researchers by ensuring UCL policy and codes of practice about data protection are implemented across all departments. |
| External Roles to UCL | ||
|---|---|---|
| Role | Responsibilities | |
| External platform providers | Responsible for the provision of storage, compute, and any associated software as a service, as defined in the environment definition of a trusted research environment.Comply with controls committed to in contract or through written agreement. | |
| Technical equipment suppliers | Responsible for providing updates to software/firmware and for complying with contractual requirements. |
Annex A - Suitable Training Resources #
| Role | Training | Link |
|---|---|---|
| Approved Researcher | NHS Digital Data Security Awareness | https://portal.e-lfh.org.uk |